Secure Communication for Embedded Devices: Best Practices for Bootloader and Application
Communication between the microcontroller's (MCU's) bootloader (BL) and
server (SRV) that run at some online virtual machine can be secured.
There is only one secret that needs to be properly secure and that is
Preshared Key on both sides.
Here I'll explain how we implemented secure communication between IMBootloader and our servers.
I'll
start with Preshared Key. It is a key that is stored at the SRV and the
BL. It is only a preshared piece of information that will make sure
both BL and SRV can communicate securely with each other. The Preshared
Key is the same on both sides.
On the SRV side, there are many
different methods to secure the key, and only the person who has access
to the server can get to it. The more problematic part is BL which will
arrive to users at Hardware device. This is when Preshared Key is exposed. This is where FLASH read
protections get in handy. For STM32 MCUs there is LEVEL2 protection that
will make sure everything that is stored at FLASH can not be accessed
with a debugger.
After Preshared Key is secured we need to make
sure that the communication channel between BL and the SRV is protected.
Since anyone can intercept the data, we would like to avoid sending
firmware that is encrypted with the same key. This is why we calculate
the key for encryption each time we initiate communication with the
server and we will call it Shared Key. The Shared key is calculated both
on BL and SRV sides but never sent over the communication. There are
strong cryptographic methods that we are using to make sure that Man In
The Middle (MITM attack) can't intercept communication or use our data
later.
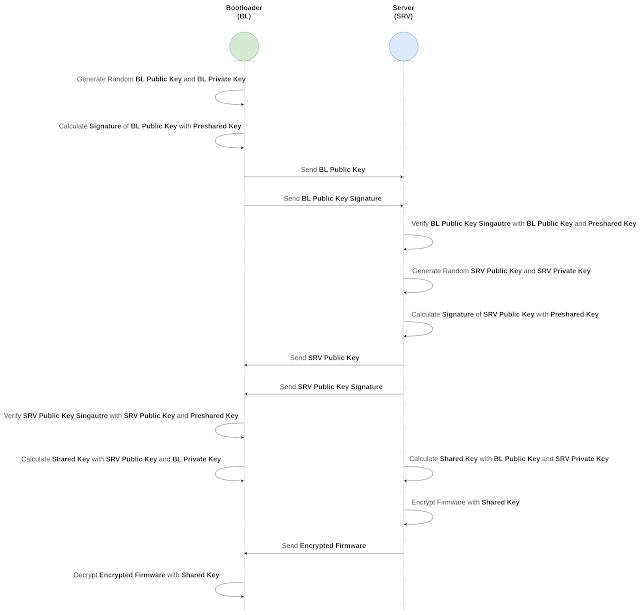
The first step is key exchange. Both BL and SRV are generating random Public and Private Keys. Then they exchange Public Keys. To be sure keys are relay generated buy trusted side, keys are sent together with the signature. Once each side receives Public Keys it can verify if the sender used the same Preshared Key. If everything has been verified both sides will proceed with creating Shared Key. Shared Key is calculated on both sides, and since the result is the same it can be used for data encryption and decryption.



Comments
Post a Comment